Just one of the many reasons my vocation and avocation is centered on information security is that things tomorrow will not be quite the same as they were today. There is always someone innovating out there for better or worse. I cannot imagine this challenge subsiding which is quite thrilling and for some, quite distressing.
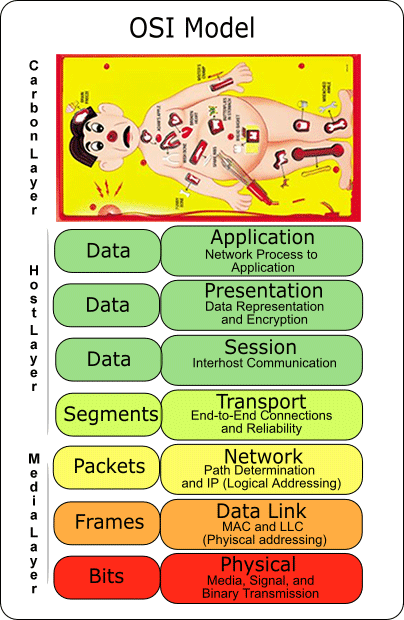
Any technologist interested in or dedicated to security and privacy probably has a decent grasp on the traditional seven layers of the OSI model. While these seven layers are purely concentrated with technology, the thing that is missing would be anything outside of that technology with absolute influence over it. I’m suggesting the addition of the human layer (aka carbon layer) be added to the model as my illustration depicts.
With the event horizon of the singularity between humans and their technology rapidly approaching, it’s time we addressed the really weak link in the OSI model; the Carbon Layer.
On its own, technology did nothing, went nowhere and was completely useless until humanity ignited the spark. While playing with fire is at times quite exciting, we all should anticipate getting burned from time to time which requires some contingency planning assuming you are wise.
While the Carbon Layer does for the most part well enough traversing the layers of technological complexity, it’s also this complexity that provides opportunities for manipulation by would-be social engineers and criminal tricksters.
Every organization is vulnerable to the threat of carbon layer manipulation. Companies are vulnerable because the individual is vulnerable. It is also widely held that the single most effective way to thwart social engineers is through awareness education. A security-aware culture is possible in any organization and any individual as long as it is the standard by which everyone operates and concepts are consistently reinforced. Here are some ways to build a culture of security. With this in mind, here are some simple suggestions to reduce these risks.
Organizations and individuals reduce their security risks by:
- Establishing awareness programs that bring the message to the individual. When it becomes personal, people remember these guidelines better.
- Identifying which information is sensitive and evaluating its exposure to information leakage. You should be doing this already as part of a proper IT risk assessment. You need to understand the value of information in order to appropriately protect it.
- Establishing security protocols, policies, and procedures for handling sensitive information. Start with governance documentation and then implement that written plan.
- Training employees in security protocols relevant to their position. Your message will only be effective if you make it applicable to the individual.
Performing unannounced, periodic tests of the security strategy in place. This includes things like a clean desk policy, phishing tests, baited USB testing, etc. - Using a waste management service that has dumpsters with locks on them, with keys to them limited only to the waste management company and the cleaning staff. Locating the dumpster either in view of employees such that trying to access it carries a risk of being seen or caught or behind a locked gate or fence where the person must trespass before they can attempt to access the dumpster. Make sure to offer tips for people outside of work at home. Things like what to shred are very useful.
- Repetition works! You should revisit your awareness strategy often if you want it to be successful. A once-a-year training program will only have limited success and your business or personal success depends on how knowledgeable the carbon layer is!
There are so many opportunities for the good and the bad actors to increase their personal capabilities. It is incumbent upon the individual to take an interest in their personal success and in doing to so, it positively benefits the organization.