Just one of the many reasons my vocation and avocation is centered on information security is that things tomorrow will not be quite the same as they were today. There is always someone innovating out there for better or worse. I cannot imagine this challenge subsiding which is quite thrilling and for some, quite distressing.
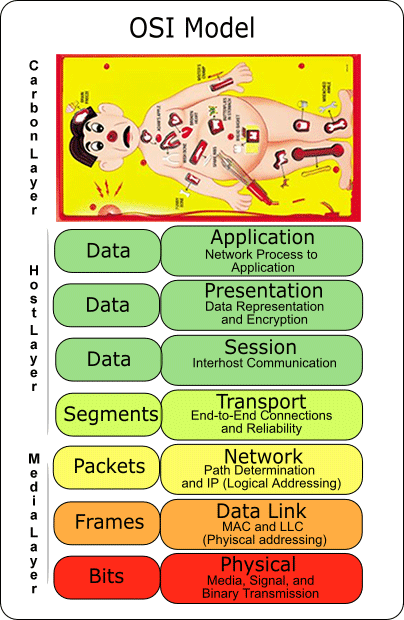
Any technologist interested in or dedicated to security and privacy probably has a decent grasp on the traditional seven layers of the OSI model. While these seven layers are purely concentrated with technology, the thing that is missing would be anything outside of that technology with absolute influence over it. I’m suggesting the addition of the human layer (aka carbon layer) be added to the model as my illustration depicts.
With the event horizon of the singularity between humans and their technology rapidly approaching, it’s time we addressed the really weak link in the OSI model; the Carbon Layer.
On its own, technology did nothing, went nowhere and was completely useless until humanity ignited the spark. While playing with fire is at times quite exciting, we all should anticipate getting burned from time to time which requires some contingency planning assuming you are wise.
While the Carbon Layer does for the most part well enough traversing the layers of technological complexity, it’s also this complexity that provides opportunities for manipulation by would-be social engineers and criminal tricksters.
Every organization is vulnerable to the threat of carbon layer manipulation. Companies are vulnerable because the individual is vulnerable. It is also widely held that the single most effective way to thwart social engineers is through awareness education. A security-aware culture is possible in any organization and any individual as long as it is the standard by which everyone operates and concepts are consistently reinforced. Here are some ways to build a culture of security. With this in mind, here are some simple suggestions to reduce these risks.
Organizations and individuals reduce their security risks by:
- Establishing awareness programs that bring the message to the individual. When it becomes personal, people remember these guidelines better.
- Identifying which information is sensitive and evaluating its exposure to information leakage. You should be doing this already as part of a proper IT risk assessment. You need to understand the value of information in order to appropriately protect it.
- Establishing security protocols, policies, and procedures for handling sensitive information. Start with governance documentation and then implement that written plan.
- Training employees in security protocols relevant to their position. Your message will only be effective if you make it applicable to the individual.
Performing unannounced, periodic tests of the security strategy in place. This includes things like a clean desk policy, phishing tests, baited USB testing, etc. - Using a waste management service that has dumpsters with locks on them, with keys to them limited only to the waste management company and the cleaning staff. Locating the dumpster either in view of employees such that trying to access it carries a risk of being seen or caught or behind a locked gate or fence where the person must trespass before they can attempt to access the dumpster. Make sure to offer tips for people outside of work at home. Things like what to shred are very useful.
- Repetition works! You should revisit your awareness strategy often if you want it to be successful. A once-a-year training program will only have limited success and your business or personal success depends on how knowledgeable the carbon layer is!
There are so many opportunities for the good and the bad actors to increase their personal capabilities. It is incumbent upon the individual to take an interest in their personal success and in doing to so, it positively benefits the organization.
Let’s not forget to count ourselves – security people – among fallible carbon units. From my experience lately, I’ve seen an increasing number of people entering into security positions who probably shouldn’t be here because they lack knowledge, skill and direct experience working in organizational/operational security. This too creates a weak link in the chain and we should work to address this as much, if not more, than working to fix others. I work as a security consultant and have been in many organizations in the last several years. I’ve seen a few disconcerting things which factor in as to why there is weak security in some organizations.
1) There is a blame game going on. If security people aren’t blaming senior management for lack of policy, lack of governance, lack of “tone at the top” they’re blaming the users for lack of awareness. Or, it’s the network team, the server team, or the developers – what they don’t know and what they’re not doing. Meanwhile the CISO, security director/manager does nothing except attend a lot of meetings and do a lot of politicking. All talk, no action. I’m seeing it all over. Colleagues of mine are seeing it too. There’s complacency, a malaise even, going on with security leadership NOT DOING anything which is becoming increasingly common. My last three engagements were with organizations who had virtually nothing in place for security. Much work needed to be done just to reach a basic level. Yet months went by with no commitment, no projects, no action plans, no remediation of control gaps/weaknesses – nothing. I don’t know how these guys get their jobs or how they keep them, or why companies continue to pay their salaries when there’s nothing to show for it after months, or even, a year.
2) There’s a perception/expectation problem. In some cases our expectations of users is too high. Not all users are technical savvy or computer literate enough to fully grasp the security concepts we are delivering in awareness training. This past summer I worked for a tribal community that had every type of employee imaginable. From healthcare workers, to fire/police/corrections, to educators/group home attendants, to public works facilities maintenance/grounds keepers/heavy equipment operators/pipe fitters/HVAC/electricians. I had to get 1200+ of these “users” through SANS Securing the Human training. All were “users” because all had user accounts created for them by IT when the organization implemented PeopleSoft employees as a service for their employees to enter time and manage their benefits, etc… I found, particularly among the public works employees that some had never once logged into their accounts. I found out why when I resorted to having classroom type sessions to help people get through this training. They didn’t know how to use a computer and some had no interest at all in computers. Some couldn’t log into the SANS training Website with the complex initial password they were given because they didn’t know how to use the keyboard. For example, one guy didn’t know how to hold the shift key and press 3 to make a # sign. I asked another guy to click on something on the screen. He wasn’t able to do it and I discovered why. He didn’t know how to use a mouse. He was pressing on the wheel. I literally had to show him where to put his finger on the mouse and press by physically placing his finger on the left mouse button. Because computers have become so interwoven into the fabric of IT and Security peoples’ lives we take it as a given that everyone needs and uses computers as we do. It’s difficult for us to imagine that some people place no importance on computers at all and want nothing to do with them. As one guy said to me, “I operate a back hoe and dig ditches. I have no interest in computers.” IT rolls out technology and gives employees access without ever considering the perspective of the employees, whether they will use it or not, whether they have the computer skills to use it or not, meanwhile creating risk by creating accounts and opening up network and system access to computer illiterate employees. So imagine the content of Securing the Human training, say, data encryption, VPNs, or public Wi-Fi, having any contextual meaning at all to a guy that doesn’t even know how to use a mouse. So take the Target breach “caused” by the HVAC guy. Whose fault is that really? The HVAC guy’s? He’s likely not a particularly computer savvy guy. Or the InfoSec manager’s? Which leads me to my 3rd factor for weak security at organizations.
3) Companies are not hiring the right security people with the right skills, knowledge, expertise – in other words: practical know-how and can-do abilities. Companies are hiring friends of someone, or a checklist auditor type who can sound like they know security, but who lack “proof is in the pudd’in” when it comes down to what they can actually do to help secure the organization. It’s easy for these types to hide in their offices, sit in their glass houses and point fingers at what the users, executive leaders, the business, developers and the various IT teams aren’t doing. But, what are they doing? The last Sr. Manager of Security I worked for actually told me with his own mouth, “I don’t need to know security. I only need to know it conceptually. It’s about perception.” This guy felt he only needed to know conceptually that logging was a good idea. He didn’t need to know how to implement proper logging and monitoring tools, configure systems for appropriate auditing/logging, or who he needed to hire and how many to hire to make effective use of a logging/monitoring capability. He had nothing in place and he didn’t seem, after nearly 6 months, that he was moving in any direction to put anything into place. One day I watched him choke in a security requirements meeting with the developers who said they wanted his advice on authentication for the new eCommerce application. The security manager (aka former checklist auditor) recited the common and mundane audit checklist item – passwords needs to be at least 8 characters and complex. What the developers were wanting was advice on authentication mechanism – i.e., SAML, OAuth, OpenID – pro’s and con’s from security’s perspective. Suddenly, the security manager was late for another meeting and had to duck out of this meeting. When I spoke later to the security manager about this the reaction I got from him was similar to the head tilt I get when I am speaking to my Pug. No clue about authentication mechanisms. Yet the irony is this guy talked a great deal about training being necessary for the developers so they could learn secure coding. So knowing that this kind of stuff is going on at a lot companies today, who’s at fault for the Target breach? The HVAC guy or the security manager who didn’t have the proper preventive and detective controls in place and know how to use them to see that data was leaving the organization? Firewall logs typically have this information if they are configured correctly. It has the external IP address and the number of bytes in the payload being transferred. There are tools available to help a human analyze log data that could have been used to identify peaks in number/size of packets going out to an external host. I’ve run into security managers and others on the security team who can’t read a simple firewall log event. No experience whatsoever with this fundamental security control. If they don’t know this one basic control, how many of the other nearly 200 other controls (i.e., ISO or NIST) do they not know a thing about at a practical, implementation and effective use level? How can these people know what is possible and appropriate for protecting a company’s systems and data if they have no experience at all with what can be done and what’s available to implement and use? Why are they in security positions to begin with? Speaking of ISO, I did and engagement at a large CoLo Data Center where the CISO had no idea what ISO was. Never heard of ISMS. How is it I conceivable that someone in charge of security at a large Data Center with nearly 800 tenants has never heard of this widely recognized, international security controls framework? You can try to say that our users are our weakest link, but from my 20+ years of information security, it’s my opinion that information security leadership is in the worst state ever due to unqualified people saturating field. Companies security programs all over are suffering for it, and ultimately, the people impacted by breaches are being harmed by it.
It’s easy to blame the users and say they need security awareness training, and spend a month or two on a 10 – 12 slide security awareness presentation on creating strong passwords. That’s show up just to collect a paycheck type work. The real work, the hard work, however, is to implement and use the necessary and proper security controls and monitoring capabilities that companies should have in place to protect themselves and their customers. But companies aren’t going to get there by hiring some guy who’s only knowledge of security is what he can repeat off the SANS Top 20 poster tacked to his wall in his office, and who’s only work experience is as an auditor operating off a controls questionnaire to fill out a checklist and write a final report from a template. To make this type of person the organizational leader in charge of security with the perception the organization now has security, when he’s never actually done security work before, is dangerous. There’s a big difference between being able to talk about doing and actually doing security. Perhaps the training that is lacking is for our own – and not just book/magazine/white paper/classroom training, but real live, hands-on, experiential training to gain practical expertise.