About Michael Peters
 Michael Peters is the CEO of Lazarus Alliance, Inc. Continuum GRC, and the HORSE Project – Lazarus Alliance Foundation, Inc. and has served as an independent information security consultant, executive, researcher and author. He is an internationally recognized and awarded security expert with years of IT and business leadership experience and many previous executive leadership positions.
Michael Peters is the CEO of Lazarus Alliance, Inc. Continuum GRC, and the HORSE Project – Lazarus Alliance Foundation, Inc. and has served as an independent information security consultant, executive, researcher and author. He is an internationally recognized and awarded security expert with years of IT and business leadership experience and many previous executive leadership positions.
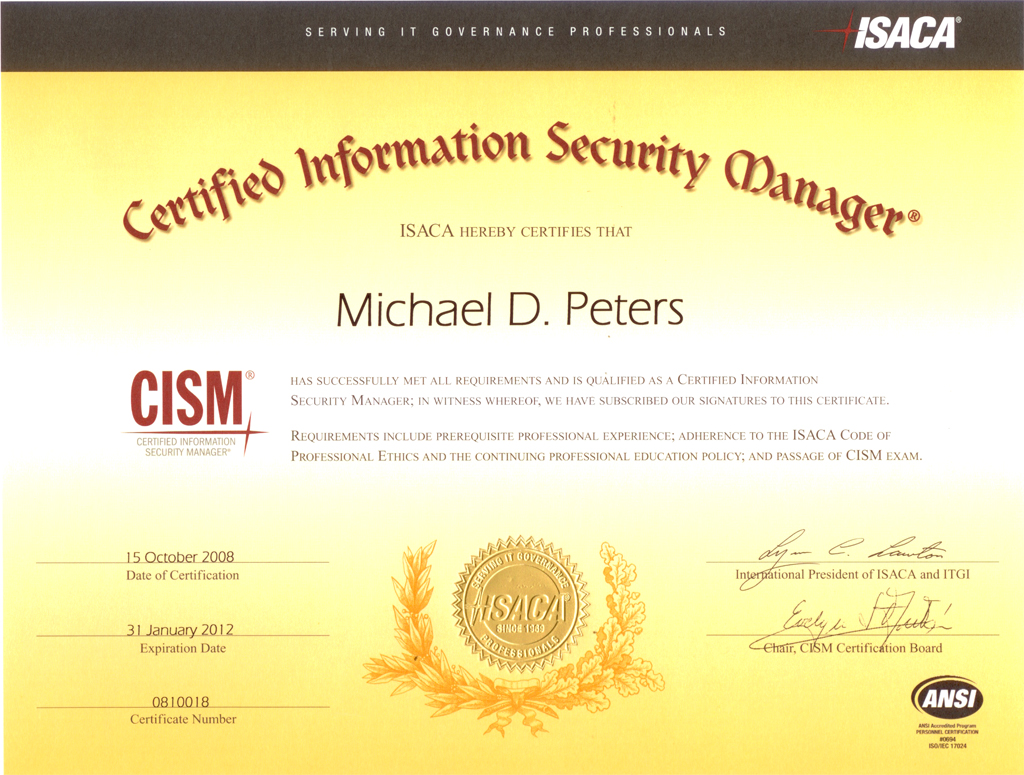
From a credential perspective, Michael holds an Executive Juris Doctor in Cyberspace Law; a certified MBA in IT Management, undergraduate degree in IT Security, CISSP, QSA, CRISC, CISM, SCPA, CCE, CMBA, SCSA and he is an ISSA Hall of Fame recipient.
Peters is the serial entrepreneur and innovator behind the IT Audit Machine (ITAM)™, the Policy Machine™, Cybervisor™, “Your Personal CXO™” information security network, the Security Trifecta™ philosophy, Survival Guidance series of audit protocols, and the globally popular Holistic Operational Readiness Security Evaluation (HORSE) Project™. He has also been responsible for a plethora of innovations, efficiencies and business enhancements for his employers throughout his career.
In the realm of thought leadership, Michael is the author of “Securing the C Level”, “Governance Documentation and Information Technology Security Policies Demystified”, “The Security Trifecta™” and thousands of blogging, tweeting, social media networking and professional network syndication and industry feature publications. He has contributed significantly towards curriculum development as adjunct professor for graduate degree information security, advanced technology, cyberspace law, and privacy programs and toward industry standard professional certifications.
He has been featured in many publications and broadcast media outlets as the “Go to Guy” for executive leadership, information security, cyberspace law, and governance. Michael’s influence reaches deep into the international business community. As a highly accomplished, senior IT corporate officer and recognized expert in IT operations, systems, data, and network security, risk and privacy, At his current career position, Michael’s leadership and influence has reached deeply into the international business community for dozens of corporations of all sizes throughout the world.
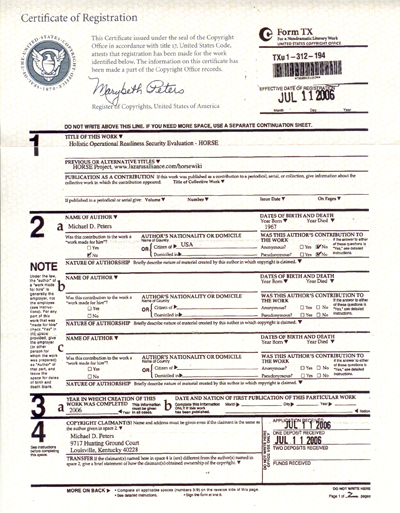
Paper Trail
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
Publications and Presentations
• Michael Peters (2017). “Understanding Future Levels of Cyber Defense.”. Presenting at the 2017 Physical & Cyber Threat Convergence Forum, Phoenix, Arizona USA.
• Michael Peters (2017). “Proactive Cyber Security Incident Response Preparations.”. Presenting at the 2017 Cyber Security Summit, Phoenix, Arizona USA.
• Michael Peters (2017). “Cyber Security – Hardware, Software, and Wetware.”. Presenting at the 2017 Accounting & Reporting Standards Conference, Phoenix, Arizona USA.
• Michael Peters (2016). “Cyber Security – A Special Focus on Cloud Computing.”. Presenting at the 2016 Phoenix Technology for Accounting Conference, Phoenix, Arizona USA.
• NBC KPNX-TV Channel 12 (2016). Ex-Teacher of the Year accused of sex with girl arrested again.. Phoenix, Arizona USA.
• Michael Peters (2016). “Trust but Verify – When GRC technology can save the day!”. Presenting at the 2016 Phoenix ISACA January meeting, Phoenix, Arizona USA.
• Michael Peters (2015). “Your Job Is at Risk: How GRC Can Save It!”. Presenting at the 2015 Phoenix Security & Audit Conference, Phoenix, Arizona USA.
• Phoenix Business Journal (2015). What small businesses and consumers can learn from NYSE, United Airlines, WSJ computer network blackouts interview. Phoenix, Arizona USA.
• NBC KPNX-TV Channel 12 (2015). Millions affected in federal cyber security breach cyber security interview. Phoenix, Arizona USA.
• EC-Council’s TakeDownCon (2015) TakeDownCon Capital Region Keynote. East Hyattsville, Maryland USA.
• NBC KPNX-TV Channel 12 (2015). Phoenix police seek Century Link cable cutter cyber security interview. Phoenix, Arizona USA.
• Michael Peters (2014). The Death of Privacy: A Tale of Collusion and Corruption. Presenting at the 2014 Phoenix Security & Audit Conference, Phoenix, Arizona USA.
• KUCI (2014). Privacy Piracy – Information Security, Cyberlaw and Privacy Issues. Interviewed by Mari Frank, Esq. on KUCI 88.9 FM in Irvine and streaming on www.kuci.org
• The New Social Security: When Social Media Meets Social Engineering, EITA Global, webinar & publication, copyright 2014
• Michael Peters (2013). The Security Trifecta: Governance Made Easy. Keynote at CISO Executive Summit, Minneapolis, Minnesota USA.
• The Security Trifecta – IT Security Governance Demystified, Pentest Magazine, publication, copyright 2012
• Michael Peters (2012). The Security Trifecta – Collaboration vs. Isolation. Keynote at Metro Louisville ISSA Information Security Conference, Louisville, Kentucky USA.
• Risky Business: IT Security Risk Management Demystified, Pentest Magazine, publication, copyright 2012
• What You Say Can and Will Be Used Against You in A …, Technorati, publication, copyright 2012
• Michael Peters (2012). The Security Trifecta – Information Security By the Numbers. Keynote at Middle East & North Africa Information Security Conference, MENA ISC 2012. Dead Sea, Jordan.
• 2012. Guest lecturer. Macon State College – School of Information Technology. The Security Trifecta – Information Security by the Numbers.
• The Security Trifecta, CrossView Connect, publication, copyright 2012.
• Consumer Reality Check – Lifting the Veil on PCI DSS, Technorati, publication, copyright 2012
• Failure to Guard Against Info Breach Leads to Firm’s Bankruptcy, Technorati, publication, copyright 2012
• InfoSec Institute – CISO Interview Series – Michael Peters, 2012.
• Peters, Michael D. (2011). The Holistic Operational Readiness Security Evaluation: HORSE Project Series Volume 1: Governance Documentation and Information Technology Security Policies Demystified. Publication. Amazon Press.
• Failure to Communicate: Pending US Congressional Orwellian Bills Threaten the Internet, Technorati, publication, copyright 2011
• Are you Alert?, Technorati, publication, copyright 2011
• Uninsured – Underinsured Information Highway Motorists, Technorati, publication, copyright 2011
• Shot Down in Flames!, Technorati, publication, copyright 2011
• The Death of Privacy?, Technorati, publication, copyright 2011
• Would You Buy a Car Without Seat Belts, Technorati, publication, copyright 2011
• Michael Peters (2011). Technorati staff writer.
• Michael Peters (2011). Coding Standards for Security. Presentation at the CrossView V4 Las Vegas Nevada Conference.
• The PCI Challenge, CrossView Connect, publication, copyright 2011
• PCI DSS Compliance in the Cloud – A Primer on New Guidelines, CrossView Connect, publication, copyright 2011
• Weapons of Mass Disruption, CrossView Connect, publication, copyright 2011
• What’s in a Name?, CrossView Connect, publication, copyright 2011
• Mobility Madness: Securely Extending Commerce to Mobile Users, CrossView Connect, publication, copyright 2011
• Your Personal CISO, Linkedin.com, Web Group, 2011
• How E-Commerce Apps Are Putting Your Site at Risk, E-Commerce Times, publication, copyright 2010
• Gearing Up for the Holidays – So Are Cyber-Criminals, CMS Article, Retail Info Systems News, copyright 2010
• Michael Peters (2010). Nothing Goofy About Security. Presentation at the CrossView Anaheim California Conference.
• 2010 ISACA CRISC Review Manual Working Group
• Peters, Michael D. (2010). Securing the “C” Level – Getting, Keeping or Reclaiming that Executive Title. Amazon Press.
• 2009 CIO Finance Summit; Guest Security Panelist
• 2009 FST 8 Summit; Guest Security Panelist
• ISSA Kentuckiana; Founding member and Past President
• ISSA Montgomery; Founding member and Past President
• 2008 CIO Finance Summit; Guest Security Panelist
• 2007 Certified MBA (CMBA) master listing of credentialed graduates.
• Board of Directors, 2002-2006, Louisville Metro Information Security Conference
• Holistic Operational Readiness Security Evaluation (HORSE); publication and wiki, copyright 2006
• Information Security forum moderator, 2006, Western Governors University Alumni
• Michael Peters (2006). Personal Privacy – Securing your identity in the wired world. Paper presented at the Independent Internal Auditors meeting
• WFPL (2006). Information Security – The Art of Deception. Interviewed with Kevin Mitnick by Rick Howlett on Public Radio Studio 619
• Michael Peters (2006). Personal Privacy – Securing your identity in the wired world. Paper presented at the Information Systems Security Association meeting
• Michael Peters (2006). Information Systems Security Association Introduction. Paper presented at the University of Louisville CIS Sophomore class spring and fall semester session
• Michael Peters (2006). Information Systems Security Association Introduction. Paper presented at the ITT Technical Institute CIS fall semester session
• Michael Peters (2005). Sarbanes-Oxley Primer. Paper presented at the Information Systems Security Association meeting
• Michael Peters (2005). Intrusion Prevention and Detection Systems. Paper presented at the Louisville Technical Institute Information Security fall semester session
• Michael Peters (2004). Passive Ethernet Tapping, Publication, Sun Microsystems
• Michael Peters (2004). Persistent IP Forwarding, Publication, Sun Microsystems
• Michael Peters (2004). Persistent IP Routing, Publication, Sun Microsystems
• Michael Peters (2004). Stealth Interface Ethernet, Publication, Sun Microsystems
• Michael Peters (2004). Authentication Security Alerting, Publication, Sun Microsystems
• Michael Peters (2004). Ethernet Network Interface Security, Publication, Sun Microsystems