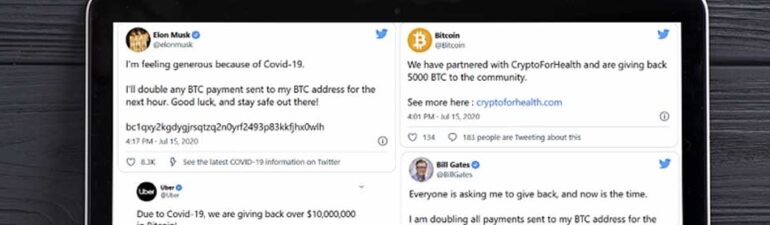
One of our country’s more important assets is its information. The U.S. IT infrastructure carries private information covering things like financial information, private information, defense and military information or information that is critical to the operation of government agencies. Some information is classified, and some, while not deemed sensitive enough to classify, are protected as… Read More