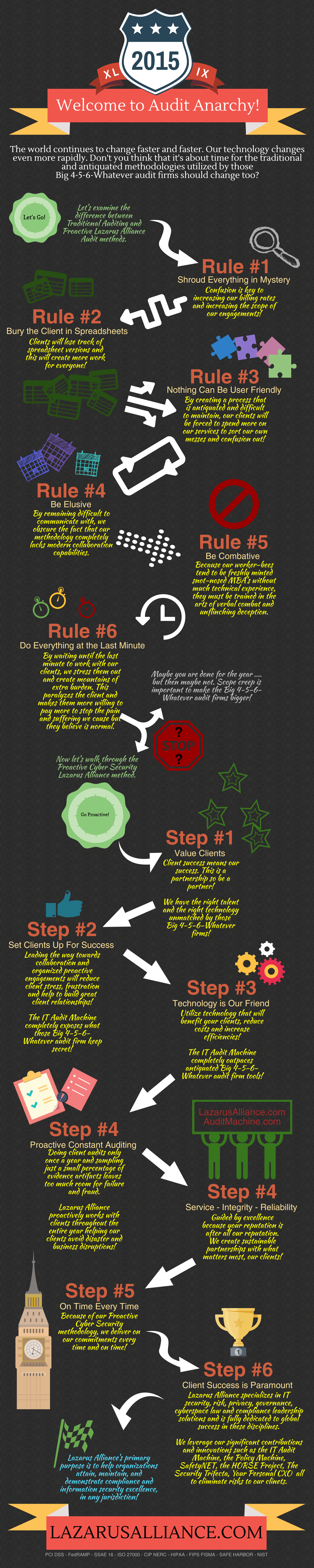
There is a huge difference in the very traditional methodology used by almost all audit firms and the proactive constant auditing methodology used by Lazarus Alliance. This infographic explains those differences along with shining a little light on some dirty techniques used by the big expensive bully firms.